Here’s a story about how one of my personal accounts was hacked and how I handled the incident.
What happened?
On the morning of May 10th 2024, I received an email from Microsoft.
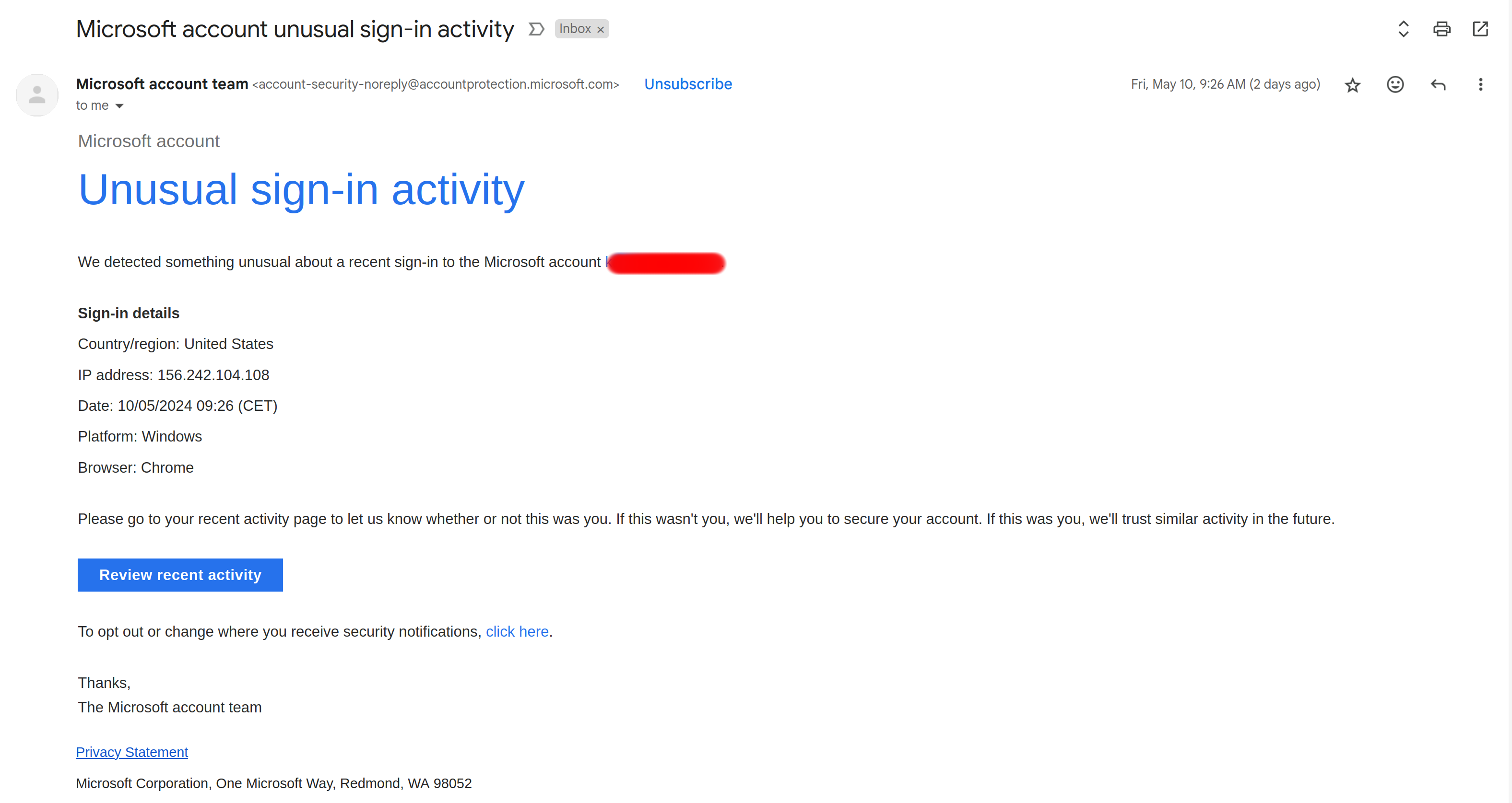
I thought this was very odd, because I don’t really use Microsoft services.
At first I suspected a phishing attempt. I checked the sender’s email address, the links included in the email, the email’s SPF & DKIM compliance. Everything looked fine.
Then I remembered that a very long time ago, before I started my career in security, I had opened a Microsoft account. So, the phishing hypothesis doesn’t seem to stand here.
So I decided to log into my Microsoft account. Out of an abundance of caution, I looked up the Microsoft Live login link on Google, that way I don’t have to trust the weird email. I found the login page, and typed in my email. I then looked up the password on my Keepass; fortunately, I had kept in my Keepass! Unfortunately, it was a very weak password indeed.
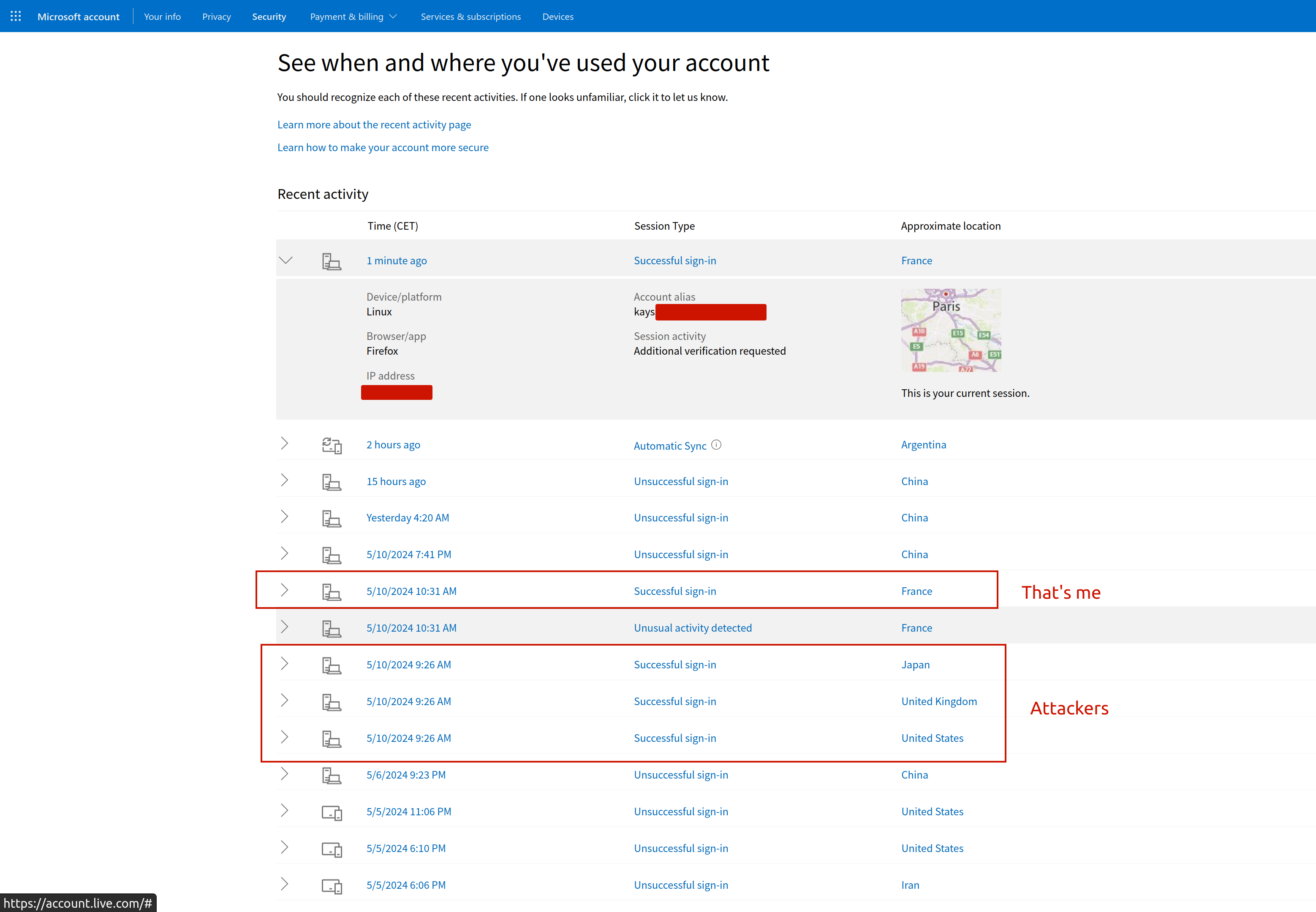
Once logged in, I went to the account’s security page, and saw that there were 3 successful login attempts from Japan, USA & UK. Yet, here I was in sunny France.
What was the impact?
Fortunately for me, nothing. This account was not used in the last 10 years, and even before that, I did not use it much.
Fixes applied?
When I saw the successful login attempts, I used Microsoft’s unusual sign-in feature to indicate a compromise. I then rotated my password. These 2 actions automatically cut off any sessions anyone had opened on my account.
Now what?
My account did not have 2FA enabled. If someone has managed to log into the account, it means my password is compromised. So the important question now is: did I use this old password anywhere else?
To answer this question, I went through all the items in my password manager to find any accounts with the same password. I was quite delighted that I had diligently added every account on there during the last decade. I ended up finding that I indeed had 3 accounts with the same weak password:
- Microsoft
- La Poste
- Hertz Car Rental
I immediately logged into my La Poste & Hertz accounts, and rotated the passwords.
What about 2FA?
I enabled 2FA on my La Poste account.
Hertz’s website did not have any 2FA support, so I closed the account.
To activate 2FA on your Microsoft account, Microsoft forces you to install their own proprietary 2FA app. Thanks, but no thanks. I closed my Microsoft account too.
What went well
- I reacted quickly to Microsoft’s email alert
- I had all my accounts listed in my Keepass
- This allowed me to see which accounts had the same weak password
- The affected accounts were not “critical” or important assets for me (unlike my private Gmail account for example)
What didn’t go well
- I used the same weak password on multiple services (I was young and foolish)
- I did not have 2FA enabled
- Microsoft pushes a proprietary 2FA app. Why do we even bother with standards…
Takeaways
For individuals
This story highlights the importance of:
- Using strong passwords
- I suspect Hertz to have been hacked. I trust Microsoft & La Poste more than I trust them.
- I’m curious to know whether this will show up someday on HaveIBeenPwned.
- Their poor security combined with my weak password meant that my password was cracked or stolen.
- Had I had a stronger password, it might have resisted cracking (assuming Hertz hashed the passwords).
- I suspect Hertz to have been hacked. I trust Microsoft & La Poste more than I trust them.
- Using 2FA
- It would have prevented this incident
- Using a personal password manager
- It allows you to keep an inventory of all your online accounts
- It obviously stores stronger passwords than your memory can ever hold
For software products
Software products can also learn from my mishap:
- Standards are important
- Microsoft lost me as a user because they wanted to force feed me their ecosystem
- Allowing the user to manage their own security is very valuable
- 2FA, Audit trails, suspicious activity alerts, proper session management etc.
